Security views determine what a user can see for a particular system or company resource. For example, at the system level you might want to limit which of your companies a user can see. At the company level, you might want to restrict a user from seeing payroll data for executives. Multiple users can be assigned to a security view.
Security view restrictions are based on user-defined conditions. While a permission can grant access to a resource, a security view can limit the scope of that access.
Example
Company security view. Suppose a user has access to the Employees resource but you want to restrict their access to only those employees whose marital status is married. You could write a condition that states that users with the security view can only view information for employees for which marital status equal married. Information for unmarried employees would not be available to users assigned to the security view.
Multiple security views on a single resource can be assigned to a single user. This means you can assign security views to a user based on exactly what the user is allowed to see. The behavior of security views on a resource can be summarized as follows:
- If no security views on a resource are assigned to a user, the user can see all rows (if the user has appropriate permissions).
- If one security view on a resource is assigned to a user, the user can only see the rows determined by the security view.
- If multiple security views on a resource are assigned to a user, the user can see the rows determined by any of the security views.
Selection conditions which refer to the items in a securable folder automatically apply the folder's security views. In particular, selection conditions can reference security views. This means that you can create security views which reference other security views and automatically apply changes to a referenced security view to the referencing security view.
Example
You can create a security view on payroll checks that limits by a user's security view on employees. If the security view on employees changes, it is automatically applied to the security view on checks.
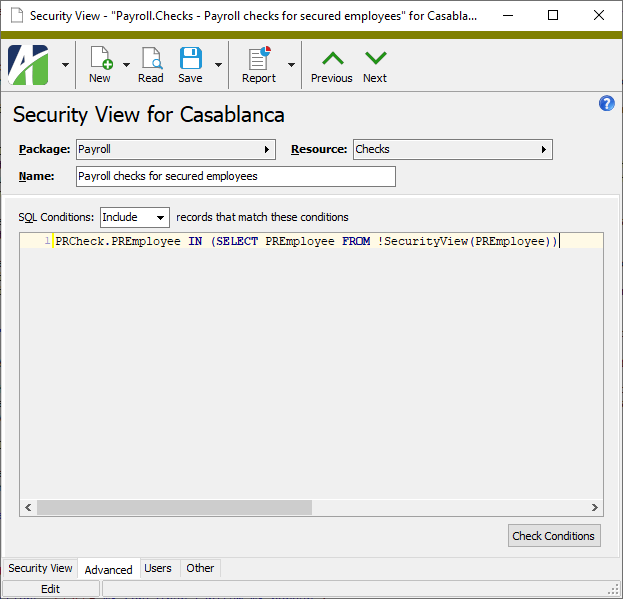
![]() Create a company security view
Create a company security view
Create a company security view
- In the Navigation pane, highlight the Administration > Security > Security Views folder.
- Click
 . The New Security View window opens.
. The New Security View window opens.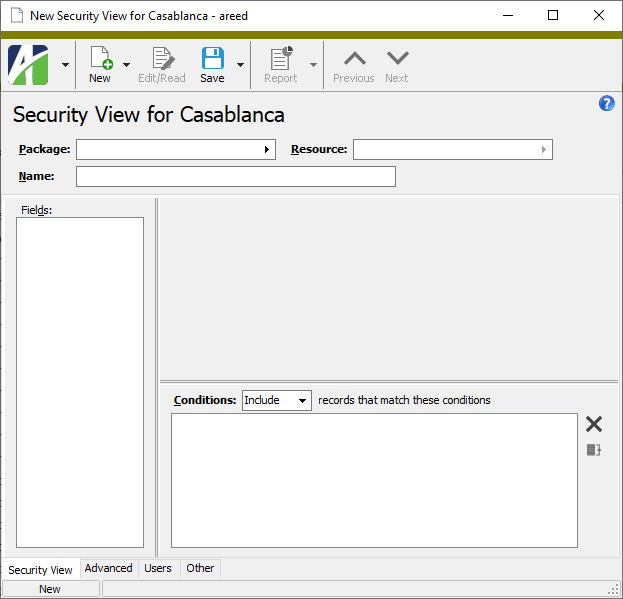
- Select the Package that contains the resource for which you want to create a security view.
-
Select the Resource to restrict with the security view. The Fields list box loads with the selection options available for filtering the selected resource.
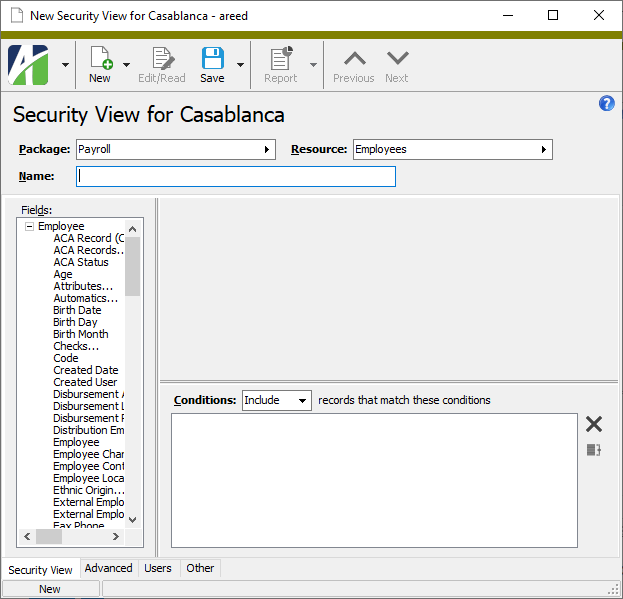
- Enter a Name for the security view. The name must be unique with respect to the selected resource.
-
Define the filters you want to apply to the data. The conditions you define load in the Conditions text box.
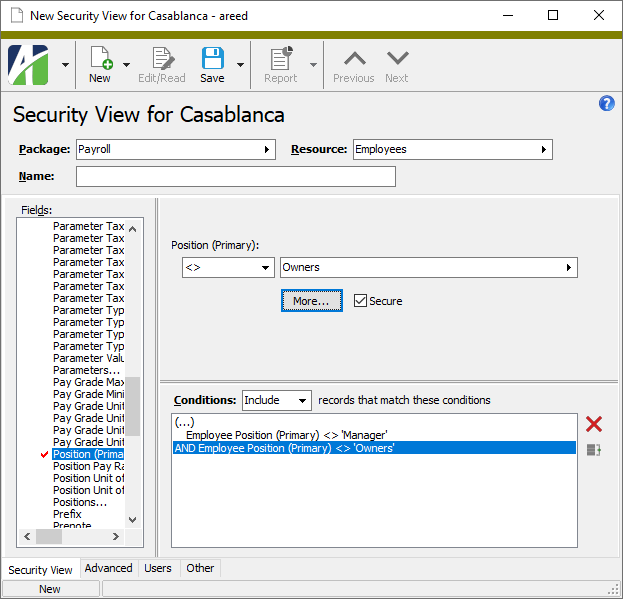
A Secure checkbox is included on some entities where the application of the user's security view potentially could cause confusing results. This is particularly likely when the defined conditions are used to exclude records that match the conditions. The Secure checkbox is marked by default; however, if you are excluding records that match your conditions, consider clearing the checkbox.
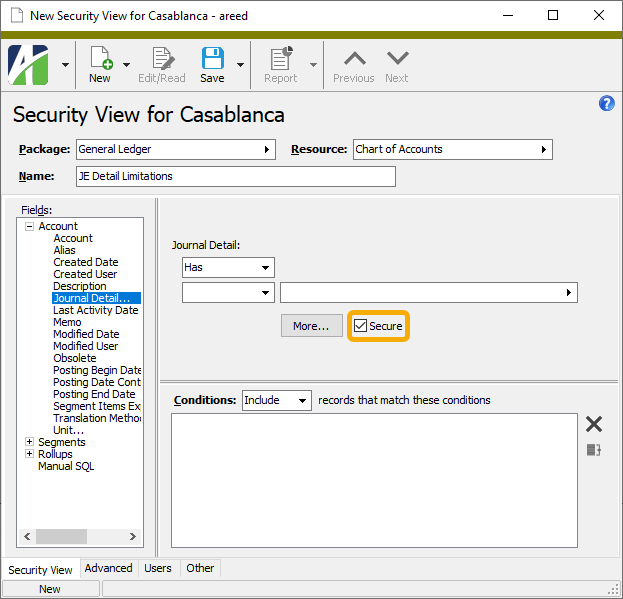
- In the dropdown above the Conditions text box, select whether to "Include" or "Exclude" the records selected by the SQL conditions you constructed.
-
Select the Advanced tab.
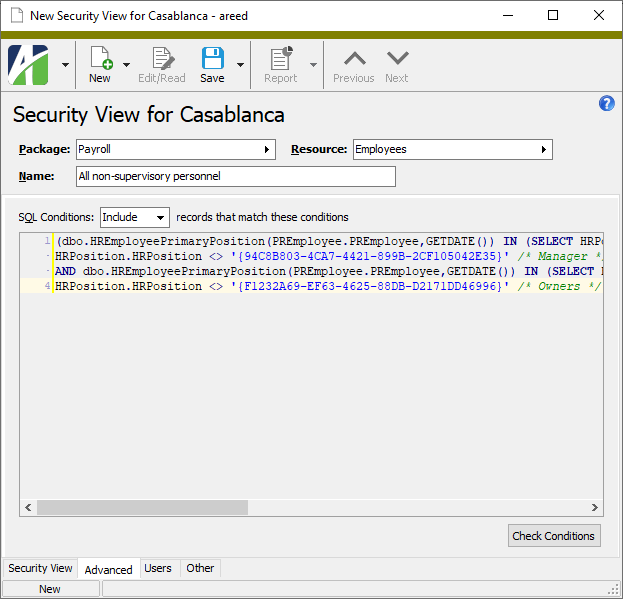
-
Click Check Conditions to verify that your conditions are well-formed. This is particularly important if your conditions include manual SQL statements. If ActivityHD advises you of problems, fix them. Once your conditions are satisfactory, ActivityHD advises you that no errors were found.
Note
The statements in the Conditions text box form the predicate of a SQL WHERE clause.
- Click OK.
- Save the new security view.
![]() Assign authorized users to a security view
Assign authorized users to a security view
Assign authorized users to a security view
- Open the security view record to which to assign authorized users.
- Select the Users tab.
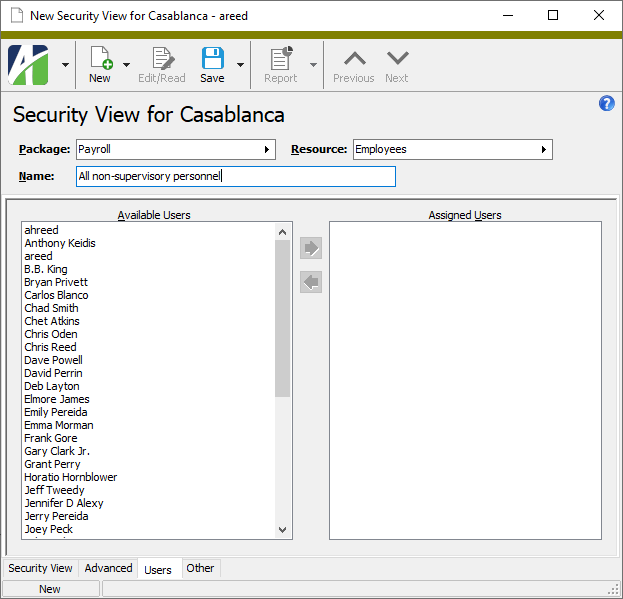
- In the Available Users list box, highlight the users to assign to the security view. You can use Ctrl and/or Shift selection to select multiple users.
- Click
 to move your selections to the Assigned Users list box.
to move your selections to the Assigned Users list box. - Save your changes.
Security Views Listing
Purpose
The Security Views Listing provides a list of security views defined for a company.
Content
For each security view included on the report, the listing shows:
- package
- resource
- security view name
- conditions type ("Include" or "Exclude").
In addition, you can include one or more of the following:
- conditions defined on the views
- users assigned to the views
- timestamps
- memos
- custom fields
The following total appears on the report:
- record count.
Print the report
- In the Navigation pane, highlight the Administration > Security > Security Views folder.
- Start the report set-up wizard.
- To report on all or a filtered subset of security views:
- Right-click the Security Views folder and select Select and Report > Security Views Listing from the shortcut menu.
- On the Selection tab, define any filters to apply to the data.
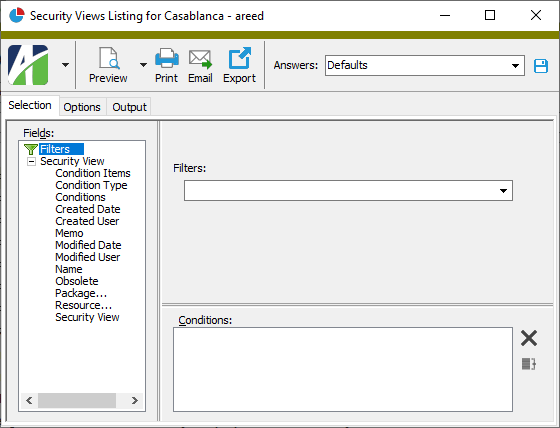
- To report on specifically selected security views:
- In the HD view, select the security views to include on the report. You can use Ctrl and/or Shift selection to select multiple records.
- Click
 .
.
- To report on a particular security view from the Security View window:
- In the HD view, locate and double-click the security view to report on. The Security View window opens with the security view record loaded.
- Click
 .
.
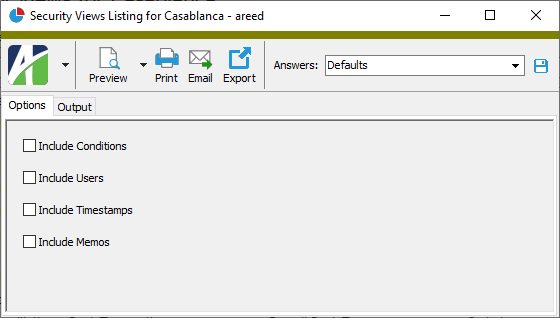
- To report on all or a filtered subset of security views:
- On the Options tab, mark the checkbox(es) for the additional information to include:
- Conditions
- Users
- Report Options. To include a section at the end of the report with the report settings used to produce the report, leave the checkbox marked. To produce the report without this information, clear the checkbox.
- Timestamps
- Memos
- Custom Fields (only visible if custom fields are set up)
- Select the Output tab.
- In the Design field, look up and select the report design to use.
- In the toolbar, click the icon for the type of output you want:
 - Provides access to two preview options.
- Provides access to two preview options.- Preview - Click the icon or click the drop-down arrow and select Preview from the drop-down menu to view the report in the Crystal Reports viewer.
- Preview to PDF - Click the drop-down arrow next to the icon and select Preview to PDF to view the report in the PDF reader.
 - Opens the Print dialog so that you can select and configure a printer and then print a paper copy of the report.
- Opens the Print dialog so that you can select and configure a printer and then print a paper copy of the report. - Opens the Report Email dialog so that you can address and compose an email that the report will be attached to. For best results, ensure your email client is running before you attempt to send a report via email.
- Opens the Report Email dialog so that you can address and compose an email that the report will be attached to. For best results, ensure your email client is running before you attempt to send a report via email. - Opens the Export Report dialog so that you can save the report to a file. File types include Crystal Reports (.rpt), PDF (.pdf), Microsoft Excel (.xls), Microsoft Word (.doc), rich text (.rtf), and XML (.xml).
- Opens the Export Report dialog so that you can save the report to a file. File types include Crystal Reports (.rpt), PDF (.pdf), Microsoft Excel (.xls), Microsoft Word (.doc), rich text (.rtf), and XML (.xml).
Data extensions
The following data extension is available for the report:
- Security views
Security View Record ID
Press F3 to look up the value.
If a value is already selected, you can press F4 to open the record in its native editor.
Press F3 to look up the value.
If a value is already selected, you can press F4 to open the record in its native editor.
Security View tab
This text box shows the conditions that will be applied on the selected resource for this security view. The conditions constitute the WHERE clause of a SQL SELECT statement.
Advanced tab
This text box shows the conditions that will be applied on the selected resource for this security view. The conditions constitute the WHERE clause of a SQL SELECT statement.
Users tab
The list box shows the users available for assignment to the security view.
To assign a user to the security view, double-click the user name to move it to the Assigned Users list box or highlight it and click ![]() to move it to the Assigned Users list box.
to move it to the Assigned Users list box.
The list box shows the users currently assigned to the security view.
To unassign a user, double-click the user name to move it to the Available Users list box or highlight it and click ![]() to move it to the Available Users list box.
to move it to the Available Users list box.
Custom tab
This tab is visible if custom fields exist for the entity. At a minimum, if there are custom fields, a Fields subtab will be present. One or more additional categories of subtabs may also be visible.
Fields subtab
This tab prompts for values for any custom fields set up for entity records of this entity type. Respond to the prompts as appropriate.
References subtab
This tab is visible if other records reference the current record.
Example
Suppose a custom field exists on PRCodes that references an ARCode. On the ARCode record, on the Custom > References subtab, you can view all the PRCodes which reference that ARCode.
Exchange Folder subtab
This tab is visible only if you set up a custom field with a data type of "Exchange Folder". The label on this tab is the name assigned to the custom field.
This tab shows the contents of the specified Exchange folder.
File subtab
This tab is visible only if you set up a custom field with a data type of "File". The label on the tab is the name assigned to the custom field.
This tab renders the contents of the specified file according to its file type.
Internet Address subtab
This tab is visible only if you set up a custom field with a data type of "Internet Address". The label on this tab is the name assigned to the custom field.
This tab shows the contents of the specified web page.
Network Folder subtab
This tab is visible only if you set up a custom field with a data type of "Network Folder". The label on this tab is the name assigned to the custom field.
This tab shows the contents of the specified network folder.
Attachments tab
The Attachments tab is visible if any record for a given entity has an attachment. If the Attachments tab is not visible, this implies that no record of the entity type has an attachment on it; however, once an attachment is added to any record of the entity type, the Attachments tab will become available.
Change Logs tab
This tab is visible if the user has "Change Logs" access to the associated data folder resource.
The Change Logs pane shows the Change Logs HD view filtered to show all change logs for the selected entity record.
Double-click a row in the pane to drill down to its record in the Change Log window.
Other tab
Developer tab
This tab is visible only when developer features are enabled.
Automation subtab
This subtab shows field names and values for the current data record. Use the information in the subtab to assist when creating automation objects such as bots and import files. The field names and field values can be copied from the text box and pasted directly into your code or application. To copy content from the text box, highlight the content to copy and press Ctrl+C or right-click your selection and select Copy from the context menu.
Export (XML) subtab
This subtab shows the XML syntax for exporting the selected data record. The syntax can be copied from the text box as an exemplar for creating your own automation objects for bots, import files, ActivWebAPI, etc. To copy content from the text box, highlight the content to copy and press Ctrl+C or right-click your selection and select Copy from the context menu.
Import (XML) subtab
This subtab allows you to select a file for import and shows the XML syntax for importing data records. Use the subtab to explore the XML syntax for importing data records. In particular, you can investigate the syntax which results when using Data.Import and ActivWebAPI data POST and DELETE routes.
Change Log (XML) subtab
This subtab is visible only when the Enable Change Logs option is marked in System Options or Company Options (depending on whether the feature applies at the system or the company level). This is the default setting when developer features are enabled.
This subtab allows you to investigate changes to the current data record. The syntax can be copied for use in bots, dashboards, ActivWebAPI, and other automation. To copy content from the text box, highlight the content to copy and press Ctrl+C or right-click your selection and select Copy from the context menu.
Select Statement (SQL) subtab
This subtab allows you to investigate the SQL select statement used to retrieve the current data record. The syntax can be copied as an exemplar for data sources and other automation. To copy content from the text box, highlight the content to copy and press Ctrl+C or right-click your selection and select Copy from the context menu.

|
Extras\Payroll\PR Security Views for allowed employees.xml; Extras\Human Resources\HR Security Views for allowed employees.xml |
Security views security
Common accesses available on security views
| Access | A user with this access can... |
|---|---|
| Change | Use the mass change action on security views. |
| Change Logs | |
| Custom Fields | Create and edit custom fields for security views. |
| Data | Have read-only access to security views from anywhere in the software (e.g., field validations, filters, date expressions). |
| Delete | Delete security views. |
| Edit | Edit security view records. |
| Export | Export security view records from ActivityHD. |
| Import | Import security view records into ActivityHD. |
| New | Create new security view records. |
| Read | Have read-only access to security view records. |
| Report | Run reports with security view information. |
| Report Designs | Create and edit report designs with security view information. This access enables the Report Designs button on the Output tab of report dialogs. |
| Shared Answers | Create and edit saved answers related to security views. |
| Shared Filters | Create and edit shared filters on security views. |
| Visible | View the Security Views folder in the Navigation pane. |
Report Email dialog
- Windows user default account. Sends email using the user's Windows default email account. For most users, this is the account configured in Outlook or another email client application.
- Server personal. Sends email using the email configuration for the system or company server and the email address on the current user's authorized user record. The authorized user record must have a confirmed email address.
- Server generic. Sends email using the email configuration and "from" address for the system or company server. This option requires "Send generic" access to the Server Email resource.
|
5225 S Loop 289, #207 Lubbock, TX 79424 806.687.8500 | 800.354.7152 |
© 2025 AccountingWare, LLC All rights reserved. |